Social engineering, according to its basic meaning, is the psychological manipulation of people with the primary goal of acquiring and disclosing confidential business and personal information.
It’s unnerving to think social engineering can happen anywhere and to anyone, but you can take steps to protect yourself and your business’s confidential sensitive data.
It starts with understanding social engineering attacks.
Social engineering methods range from simple to complex, but they all rely on human emotions and trust.
This post will cover the multiple social engineering techniques and ways to defend against losses.
What Actually Is Social Engineering, and Why Does It Occur?
Social engineering attacks all share one goal: to get information or access from a user through human interaction. They do this using three key methods: imitation, intimidation, and manipulation.
The most successful social engineers play on emotions to lower the victim’s guard.
The attack typically begins with a well-crafted email or phone call. The sender has done their research and knows enough about you to make the message seem believable.
For example, they may claim that your computer is experiencing technical issues, ask for credit card information to process a refund, or trick you into thinking they’re from tech support and need remote access to your computer.
Social engineering attacks occur for a variety of reasons. Valuable information such as credit card numbers, social security numbers, and other personal or financial data is sold or used on the dark web.
Another reason hackers commit cybercrime is to get access to a company’s computer systems or networks. Once inside, they can wreak havoc by altering data, wiping files (a technique known as ransomware), or illegally selling them to make money.
Finally, social engineering could be retaliation; perhaps the attacker is feeling angry, embarrassed, or jealous.
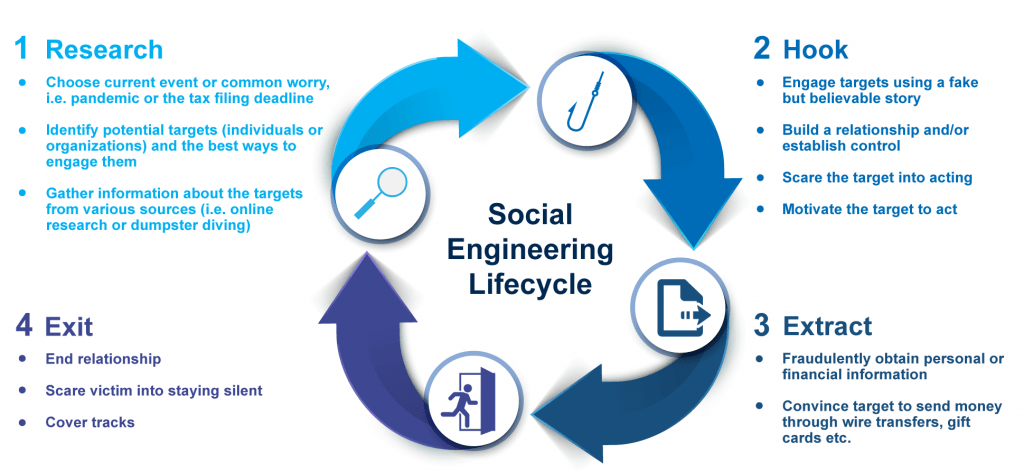
Social engineering attacks types and examples
There are many types of social engineering attacks, each of which takes advantage of a lack of awareness and understanding of the threats they pose. The most common types are as follows:
- Phishing: One of the most frequent social engineering attacks. Sending an email or text message pretending to be a genuine business in an attempt to dupe the recipient into disclosing personal information.
- Spear Phishing: Similar to phishing but explicitly targeting individuals or groups. Emails sent to the victim contain links and attachments to spread malware, steal data and escalate privileges within the system.
- Whaling (CEO Fraud): Whaling occurs when an attacker tries to trick the CEO, CFO or another highly ranked executive into giving up important information such as credit card numbers or login credentials using email or a web page with fake text.
- Baiting: It is a specific type of social engineering attack that involves putting malware (viruses, worms or Trojan horses) on removable drives such as USB sticks.
- Vishing (Voice Phishing): Vishing is an attack that uses voice technologies and messages to trick you into giving up personal information.
- Smishing attack: It is a type of phishing scam that targets mobile devices. For example, a message might say that your account is compromised, and you should text back with username and password information.
- Tailgating: This type of attack occurs when an unauthorized person follows someone with authorized access to a secure area and gains the same level of access without credentials or permission.
- Quid Pro Quo attack: A quid pro quo attack involves someone asking for your credentials in return for something (usually money).
- Watering Hole: A social engineering attack in which a hacker compromises a popular website frequented by their target and uses it to gain information about them.
- Dumpster Diving: involves attackers searching through the trash for documents holding personal or sensitive information.
- Farming vs Hunting: Hunting is the practice of gathering data from people with little or no personal interaction. On the other hand, Farming relies heavily upon establishing rapport to gain trust from their target before any real action occurs.
To keep their victims engaged in conversation, social engineers may employ humour or ask seemingly innocent questions. These are some other common signs of social engineering attacks:
- Spelling and grammar errors
- Threats or urgency
- Suspicious links or attachments
- Requesting personal information
- Misspelled email addresses or domain names similar but not identical to your own.

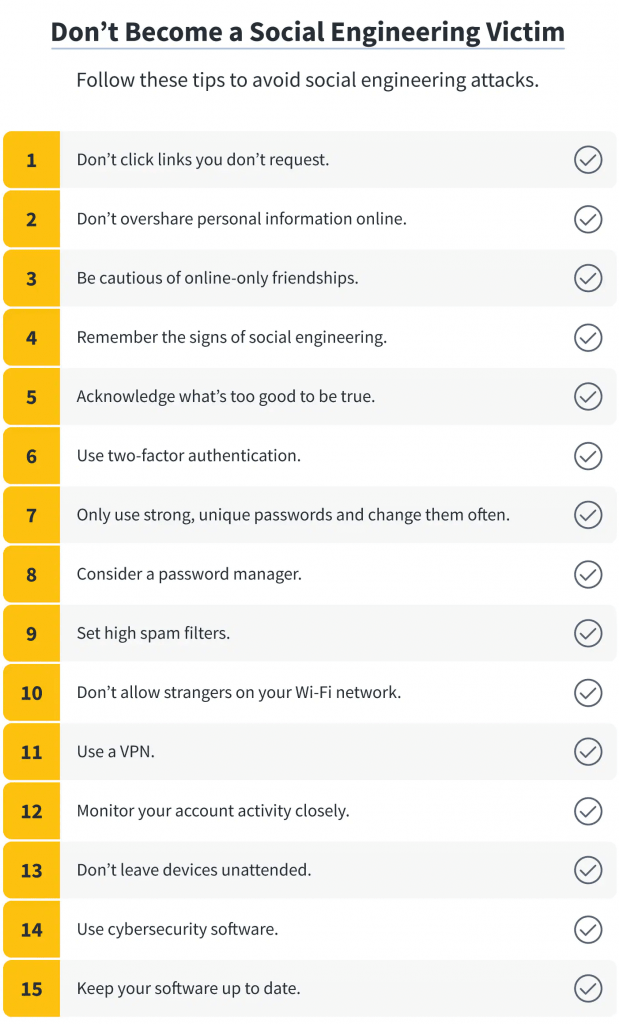
Prevent social engineering attacks by taking the following steps:
- Use different strong passwords and passphrases
- Don’t share data with too many people; reward access thoughtfully
- Educate your employees to avoid compromising company security policies
- Treat all calls, emails, or text messages as suspicious unless you’re 100%
- Have multiple defence layers to frustrate attackers’ efforts
- Keep your systems secure with software patches and updates for vulnerabilities
- Don’t open suspicious emails- hover over content URLs first
- Don’t click links you don’t request
- Be cautious of online-only friendships
- Remember the signs of social engineering
- Use two-factor authentication and multifactor authentication – an authenticator app or security key
- Consider a password manager
- Set high spam filters
- Don’t allow strangers on your Wi-Fi network
- Use a VPN
- Monitor your account activity closely
- Don’t leave devices unattended
Prevent Scam Emails Using Spam Filters
Email is a critical part of most business communications, but it’s also the number one source of cyber attacks and spam. According to Barracuda, the average organization is targeted by over 700 social engineering attacks each year.
Gateways such as SpamTitan and Barracuda assist administrators by providing protective filters which remove phishing emails and block harmful threats. With an email gateway, you don’t need to rely on expensive technology solutions or human effort for protection against malicious content.
Prevention Tips for Pretexting Victims
Pretexting is a common social engineering tactic. It involves creating a false excuse that sounds genuine; for example, an attacker calls a target firm and pretends to be from IT support.
Then, the attacker requests the employee’s name from another target, providing access credentials or other critical information. If they’re successful in getting this knowledge, it is used later in another attack.
When someone wants sensitive information from you, always ask for verification, chiefly if someone inquires multiple times about the same type of data.
Prevention of Social Engineering by cultivating Security Awareness principles inside the company
Because social engineering assaults target employees, it’s critical to educate them about the most recent threats in their field. You can help keep sensitive information safe through training, teaching people to recognize phishing emails and other suspicious behaviour.
Security awareness training teaches employees not to become a target of malicious hackers and not let cybercriminals accessing company resources. Training includes topics such as:
- What information not to share with strangers over the phone or via email
- How to protect passwords and usernames
- How to recognize phishing emails, phone calls, or text messages.
BSG security awareness training offers gamification elements (quizzes, videos, and scenarios) during the studying and is suitable for all employees, regardless of the job position they have.
Another part of security awareness is phishing attacks simulations.
It aims to employees to teach how to deal with- and protect themselves from phishing emails.
Security Awareness Training is gaining popularity and Berezha Security provides the course to our customers, as many security breaches happen due to human error rather than due to technical issues.
Be aware that social engineering attacks don’t just occur on the internet – they can happen in person as well.
Be aware that social engineering attacks don’t occur on the Internet – they can happen in person as well.
For example, a social engineer will target the weak points in a company’s security, such as staff being too friendly, not checking if someone is who they say they are, or employees not following procedures correctly.
Conclusion
People in business need to be aware of different types of social engineering attacks and how to protect themselves. It’s never too early to start safeguarding yourself and your business against attack.
With so many forms of attack, you may feel powerless to stop them.
The best way not to become a victim of malicious hackers is to get the support of professionals in social engineering and penetration testing. A penetration testing firm or certified security experts can run a controlled security attack simulation and find multiple strategies to prevent your company from becoming victims of a social engineering campaign. Find out more about how we can help you not become a victim of social engineering with BSG security services.
Don’t delay — start protecting yourself today.
Be safe.