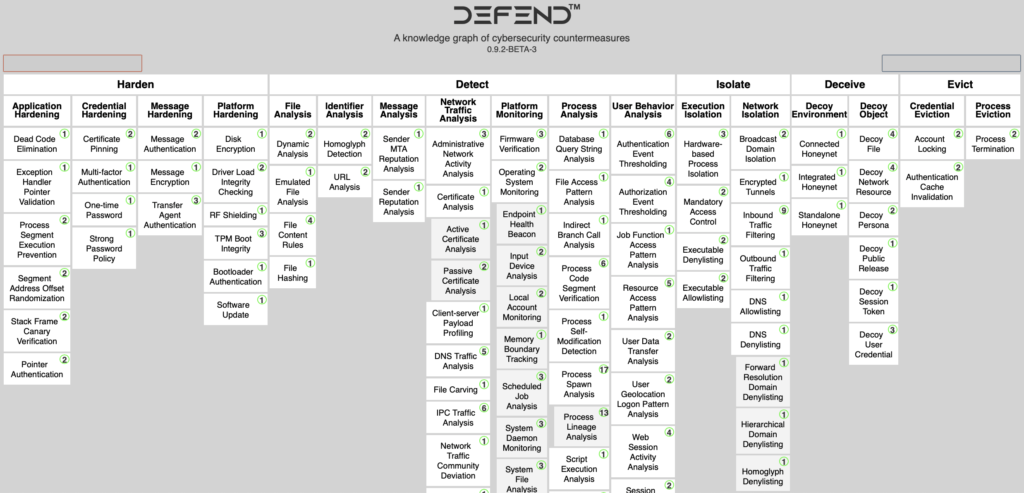
The NSA and Mitre Corporation have introduced the Mitre D3FEND framework – a matrix of defensive techniques that map to Mitre ATT&CK. ATT&CK is, of course, the well-known registry of offensive tactics, tools, and procedures. Along with offensive techniques, Mitre ATT&CK contains references to corresponding mitigation steps. As Mitre says, practitioners must know not only what threats a capability claims to address but precisely how those threats are addressed from an engineering perspective and under what circumstances the solution would work. Putting these defensive techniques into a separate D3FEND framework will help blue teamers.
The final stage of any pentesting project is providing recommendations on remediation. It is indeed the most crucial phase in every security assessment. Unless the pentest produces a report with clear guidance on improving the cybersecurity of an organization, system, or application – it is virtually useless, as awareness of vulnerability presence means nothing until you have a plan for dealing with it.
BSG does not invent remediation steps for our recommendations, as it is more of the security engineers’ job. We, the hackers, are here to find, investigate, diagnose the problem, and advise our clients on fixing it. When it comes to application security, giving advice is pretty simple. The problem is apparent in the software code or application configuration. Unlike application security, infrastructure or organizational pentest recommendations can become vaguer, as the corresponding problems can be solved on various levels.
We often find ourselves on Miter Corporation websites in search of material for our network and social engineering pentest reports. Mitre CVE database hosts a lot of reference materials about security vulnerabilities. Mitre CWE catalog helps to classify virtually any cybersecurity threat. And the Mitre ATT&CK framework allows arranging the attack narratives in orderly cyber kill chain diagrams.
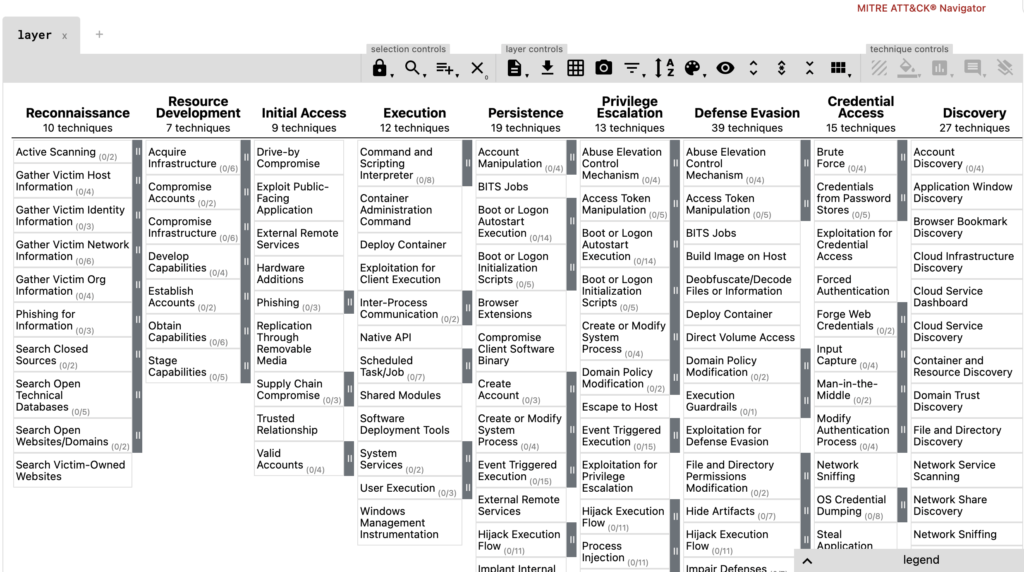
All these Mitre security projects aim at giving the defenders a clear and broad picture of what they can expect from different types of attackers. The ATT&CK framework, though, arranges data in a way that is attacker-centric, efficient for data breach responders and threat analysts but is less convenient for security engineers and managers. Simply because in the ATT&CK framework, remediation steps are preceded by lots of information about the attackers’ modus operandi and typical indicators of compromise.
The D3FEND framework solves that by putting the defensive techniques – risk controls, vulnerability remediations, and cybersecurity procedures – in the foreground and mapping them to the corresponding ATT&CK techniques. In other words, Mitre Corporation has created the mirror image of their successful product by changing the perspective. Blue team members must not mine the ATT&CK framework for relevant defensive techniques as they now have them arranged neatly and ordered.
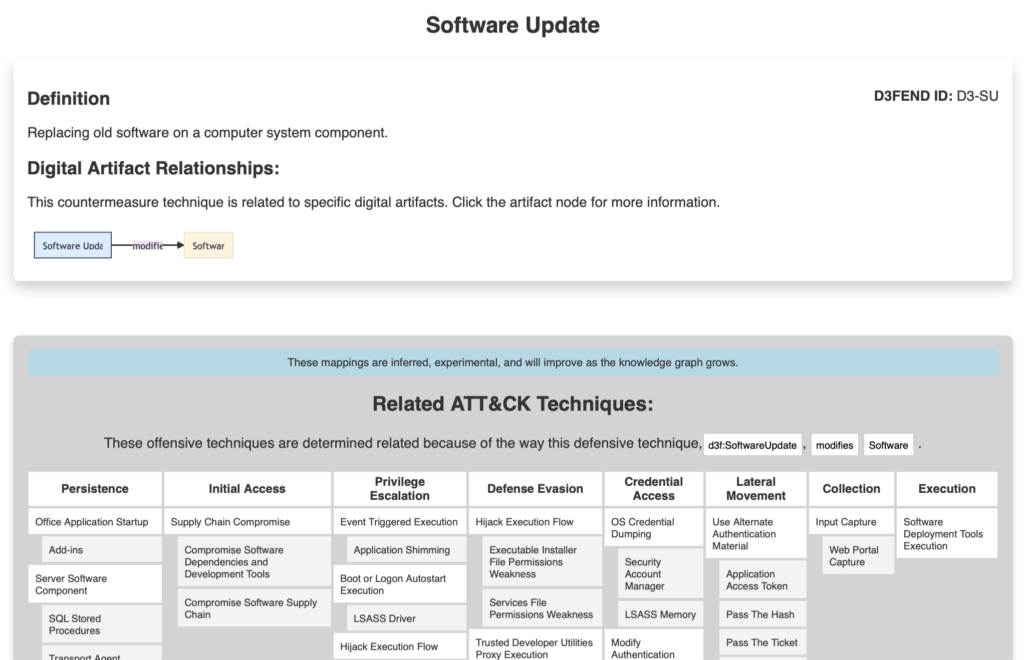
We recommend every blue team and CISO adopt the D3FEND framework into their arsenal of cybersecurity tools. And we hope to see more of our clients treating our infrastructure security assessments using this new practical approach to enterprise cyber defense.