MITRE D3FEND is a knowledge graph of cybersecurity countermeasures that gives defenders a structured way to select, organize, and communicate defensive techniques. While MITRE ATT&CK catalogs how adversaries attack, D3FEND answers the follow-up question every blue team asks: what exactly should we do about it?
First released as a beta in June 2021, D3FEND has matured into a production-grade ontology. Version 1.0 shipped in January 2025. The latest release, v1.3.0 (December 2025), contains 267 defensive techniques across seven tactical categories and includes an operational technology (OT) extension. This guide covers everything security teams need to know to put D3FEND to work.
What Is MITRE D3FEND?
D3FEND stands for Detection, Denial, and Disruption Framework Empowering Network Defense. Funded by the NSA Cybersecurity Directorate and managed by MITRE’s National Security Engineering Center (NSEC), it is an open, vendor-neutral knowledge graph built on the OWL 2 DL ontology language.
Unlike a simple checklist, D3FEND models the relationships between defensive techniques, the digital artifacts they act on, and the offensive techniques they counter. That structure lets security engineers reason about coverage gaps, compare products, and justify investments with precision that spreadsheet-based approaches cannot match.
At BSG, our penetration testing reports reference ATT&CK techniques to describe findings. D3FEND completes the picture by giving clients a structured path from each finding to the specific countermeasures that address it.
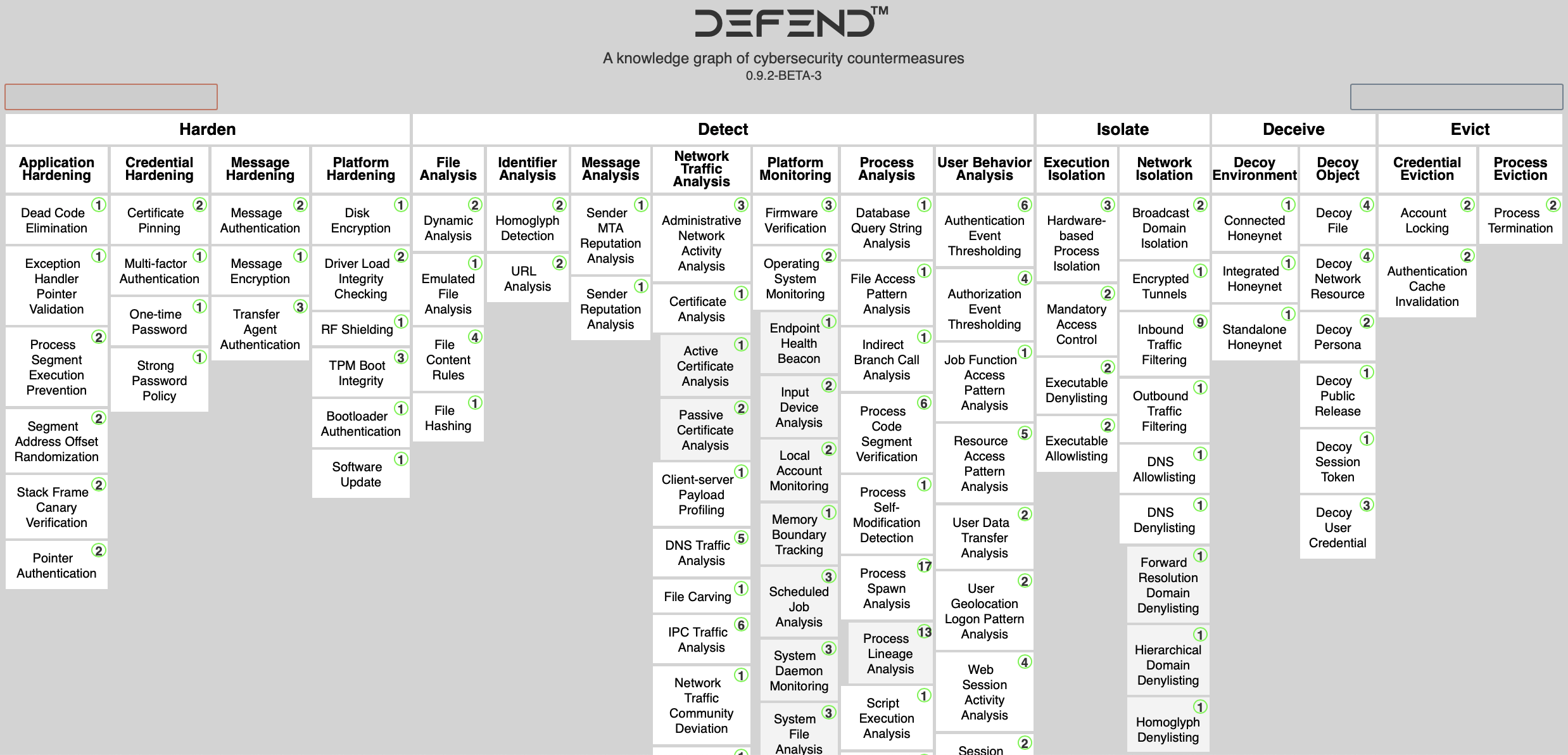
The Seven Tactical Categories
D3FEND organizes its 267 techniques into seven tactics. Each tactic represents a distinct defensive objective.
Model (27 techniques)
Asset inventorying, network mapping, and data-flow analysis. Modeling techniques help teams understand what they are protecting before they configure a single control. Examples include System Mapping, Asset Vulnerability Enumeration, and Operational Activity Mapping.
Harden (51 techniques)
Proactive measures that reduce the attack surface. This is the largest preventive category, covering Application Hardening, Credential Hardening, Platform Hardening, and Message Hardening. Techniques here include Application Configuration Hardening, Multi-Factor Authentication, and File Encryption.
Detect (90 techniques)
The largest category overall. Detect techniques identify adversary activity through monitoring and analysis. Subcategories span File Analysis, Identifier Analysis, Message Analysis, Network Traffic Analysis, Platform Monitoring, Process Analysis, and User Behavior Analysis. This is where most SOC tooling maps.
Isolate (57 techniques)
Containment and segmentation controls that limit lateral movement. Includes Execution Isolation (sandboxing, container isolation), Network Isolation (network segmentation, broadcast domain isolation), and Data Isolation. Critical for limiting blast radius after initial compromise.
Deceive (11 techniques)
Deception-based defenses such as Decoy Environments, Decoy Objects, and Decoy User Credentials. Though the smallest category, deception techniques can provide high-confidence detection signals that bypass alert fatigue.
Evict (19 techniques)
Techniques for removing adversary presence once detected. Covers Credential Eviction (credential rotation, account locking), Process Eviction, and Account Eviction. Essential for incident response playbooks.
Restore (12 techniques)
Recovery techniques that return systems to a known-good state. Includes Data Restoration, System Recovery, and Configuration Restoration. Ties directly to disaster recovery and business continuity planning.
How ATT&CK and D3FEND Work Together
ATT&CK and D3FEND are connected through digital artifacts. An ATT&CK technique targets a specific digital artifact (a process, credential, file, network connection). A D3FEND technique defends or monitors that same artifact. This shared ontology creates a bidirectional bridge.
For example, ATT&CK technique T1003 (OS Credential Dumping) targets credential artifacts. D3FEND maps multiple countermeasures to those same artifacts: Credential Hardening techniques like Multi-Factor Authentication and Credential Rotation, plus Detect techniques like Credential Compromise Scope Analysis.
This mapping allows security teams to:
- Gap analysis: Overlay current defenses against the ATT&CK techniques most relevant to their threat model.
- Product evaluation: Compare vendor claims against specific D3FEND techniques rather than vague marketing language.
- Report enrichment: Link application security findings to both the attack path and the recommended countermeasures.
D3FEND also provides a formal ATT&CK Mitigations mapping that links ATT&CK’s mitigation entries to D3FEND’s more granular technique definitions.
Key 2025 Milestones
D3FEND 1.0 (January 2025)
The 1.0 release marked D3FEND’s transition from research project to production-ready ontology. Key additions included:
- OWL 2 DL foundation with D3FEND Core Classes for alignment with upper ontologies
- CWE integration connecting defensive techniques to Common Weakness Enumeration entries, enabling vulnerability-centric defense planning
- Content lifecycle strategy providing predictable update cadences for software integrators
- The semantic graph tripled in size compared to the 2021 beta
OT Extension (December 2025)
D3FEND v1.3.0 extended the ontology into operational technology environments. Industrial control systems, SCADA, and IoT devices now have dedicated defensive techniques covering OT-specific monitoring and hardening. This addresses a longstanding gap as OT environments face increasing threats from both state-sponsored actors and ransomware operators.
The CAD Tool: Visual Attack-Defense Modeling
The Cyber Attack-Defense (CAD) tool is D3FEND’s interactive modeling environment available at d3fend.mitre.org/cad. It provides:
- Drag-and-drop diagramming for building attack-defense scenarios using D3FEND and ATT&CK nodes
- Ontology-based inference that automatically suggests related techniques when you add nodes to a graph
- STIX 2.1 import for integrating existing threat intelligence
- CAD Library for creating, sharing, and reusing graph templates across teams
- CAD IDE with JavaScript editing for advanced customization
- Pathfinder tool for exploring connections between any two nodes in the knowledge graph
- Edge verification to validate that relationships in your graph align with the formal ontology
For cybersecurity consultants and enterprise security architects, CAD provides a way to model threat scenarios visually and demonstrate defensive coverage to stakeholders who need more than a spreadsheet.
Compliance Mappings
D3FEND bridges the gap between defensive engineering and compliance requirements through semantic mappings:
NIST 800-53 Rev. 5
D3FEND techniques map to NIST 800-53 Rev. 5 security controls. This lets teams use D3FEND’s technical specificity while demonstrating compliance with the federal control catalog. Rather than asking “are we compliant with AC-2?” teams can ask “which D3FEND techniques implement AC-2, and do we have them deployed?”
DISA CCI
The Defense Information Systems Agency’s Control Correlation Identifiers (CCI) are mapped to D3FEND techniques, supporting Department of Defense compliance workflows and STIG implementation.
CWE Integration
CWE entries connect to D3FEND through vulnerability modeling. This means teams can trace a path from a specific software weakness (CWE) to the defensive techniques that prevent or detect its exploitation — and back to the ATT&CK techniques that exploit it. The full chain is: CWE weakness → ATT&CK exploitation technique → D3FEND countermeasure.
Getting Started with D3FEND
For Blue Teams and SOC Analysts
- Start with your threat model. Identify the ATT&CK techniques most relevant to your industry and environment.
- Map existing controls. Use D3FEND’s ATT&CK mapping to check which defensive techniques you already have in place.
- Identify gaps. Focus on the Detect and Isolate categories first — detection and containment are where most organizations have the largest coverage gaps.
- Use CAD for scenario planning. Build visual models of your highest-priority attack paths and overlay your current defenses.
For CISOs and Security Leaders
- Use compliance mappings. Map your D3FEND coverage to NIST 800-53 or DISA CCI to satisfy auditors with engineering-grade evidence.
- Evaluate vendor products. Ask vendors which D3FEND techniques their products implement. Reject vague claims.
- Prioritize investments. D3FEND’s structured taxonomy helps quantify which defensive categories are under-resourced.
- Benchmark maturity. Track how many D3FEND techniques you have deployed per tactic as a maturity metric over time.
For Penetration Testers
- Enrich reports. Map findings to both ATT&CK techniques and D3FEND countermeasures. This gives clients an immediate remediation path.
- Validate defenses. Use D3FEND to verify whether the controls that should have caught your attack were actually in place.
Frequently Asked Questions
What is the difference between MITRE ATT&CK and D3FEND?
ATT&CK catalogs adversary tactics, techniques, and procedures — it describes how attackers operate. D3FEND catalogs defensive countermeasures — it describes how defenders should respond. The two frameworks share a common digital artifact ontology that connects them. ATT&CK tells you what the threat is; D3FEND tells you what to do about it.
How many techniques does D3FEND contain?
As of version 1.3.0 (December 2025), D3FEND contains 267 defensive techniques organized across seven tactical categories: Model (27), Harden (51), Detect (90), Isolate (57), Deceive (11), Evict (19), and Restore (12).
Is D3FEND free to use?
Yes. D3FEND is publicly available at d3fend.mitre.org under open access. The knowledge graph, CAD tool, and all compliance mappings are free. The project is funded by the NSA Cybersecurity Directorate and managed by MITRE’s NSEC.
Conclusion
MITRE D3FEND has evolved from a beta announcement into the most comprehensive structured catalog of cybersecurity countermeasures available. With 267 techniques, formal compliance mappings, OT coverage, and a visual modeling tool, it gives blue teams the same structured advantage that ATT&CK gave red teams.
Whether you are building a detection engineering program, evaluating security products, or mapping pentest remediation, D3FEND provides the common vocabulary and ontological rigor to do it well.
Need help mapping your defensive posture to real-world threats? BSG’s penetration testing and cybersecurity consulting services deliver findings mapped to both ATT&CK and D3FEND, giving your team a clear path from vulnerability to remediation.