Demonstrating your return on cyber security investment to investors and top managers is a complicated task. But for a contemporary CISO (Chief Information Security Officer), ROSI (Return on Security Investment) is a Key Performance Indicator (KPI) and is often among their Objectives and Key Results (OKR). What knowledge exists to help you in achieving this critical business goal?
An entire scientific discipline of Cybersecurity Economics exists to research the best ways to invest in cyber security. Still, it goes far beyond what we could cover in a blog post. So, instead of constructing a return on security investment formula based on the academic material, which we will probably do another time, we have decided to share practical methods of demonstrating cybersecurity investment efficiency in real life.
But first of all, why demonstrating the effectiveness of security investment is so complicated? The answer is straightforward: otherwise, no one will be able to see it. Noticing cybersecurity efficiency is problematic: unlike software features or business objectives, which can be demonstrated by their effects on user satisfaction and overall business success, the triumph of security is obscure. Investments in features, marketing, and sales pay off or do not; but the point of investing in cyber security is less obvious.
What good indicators of return on information security investment exist? We could readily indicate five.
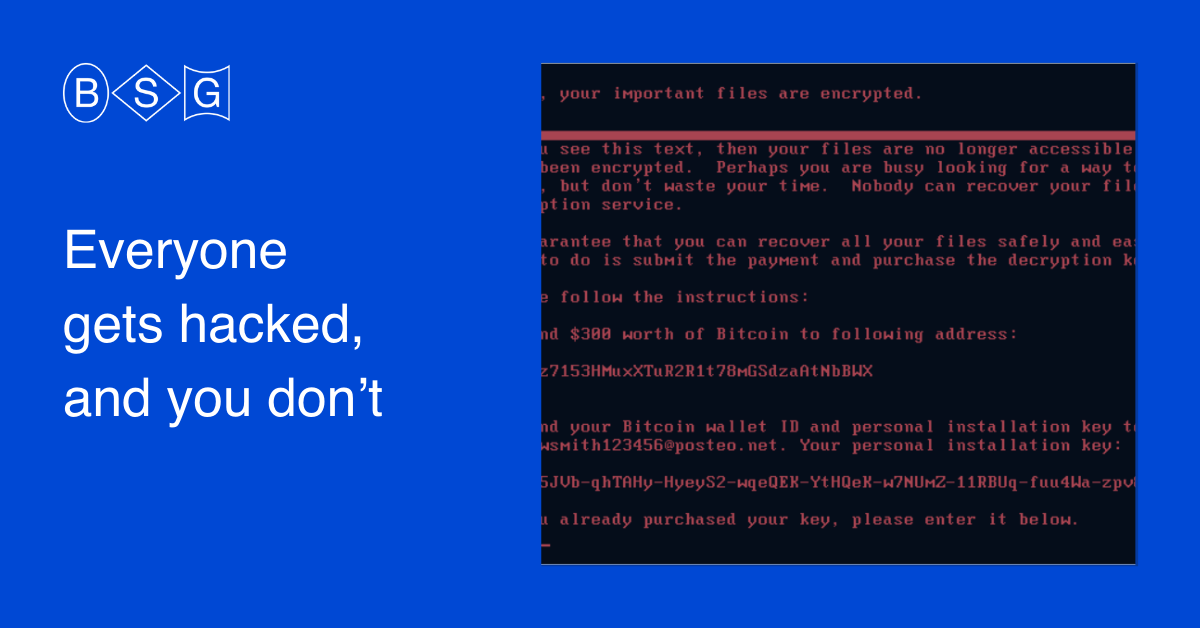
1. Everyone Gets Hacked and You Don’t
This is the simplest efficient return on security investment example: if your company’s annual loss expected as a result of cybersecurity incidents is zero, your success is self-evident. Cybercriminals herd bots in unprotected systems, ransomware attacks are on an all-time high, and if there is a vulnerability in your defenses, you are already a victim of a cyber attack: you just don’t know it yet.
Crypto extortion and data breaches are bad enough, but they may miss the target by their victims’ pure luck. From time to time, though, a global network worm pandemic happens that does not leave any stones unturned. WannaCry, NotPetya, and the mass compromise of MS Exchange servers are excellent examples from recent history.
The cost of an incident is not limited to revenue or data loss: it has long-term implications such as reputation damages and higher insurance premiums. Thus, if you are still in business, it may indicate the effectiveness of your cyber security investment.
Avoiding such a cyber tsunami for a long time is a good indicator that your security team moves in the right direction. It may not be a guarantee that your cybersecurity defenses are at the top of the world, but it objectively proves that they are way above the average.
2. You Look for the Signs of Being Hacked, and You Find None
Another valuable signal of you doing an excellent job is the lack of indicators of compromise in the assets under your management. If you pay close attention to the cybersecurity events in your apps, systems, and networks, and are not able to identify the signs of ongoing incidents, chances are there aren’t any.
One of the critical parts of this job is to have a clear vision of the threat landscape in your infrastructure. Threat management, e.g. collecting, aggregating, triaging, and analyzing security events is an essential cybersecurity business process.
Every company could benefit from establishing a Security Operations Center, but not every budget could afford the appropriate investment and talent acquisition. If your organization is too young for a SOC, there are other methods to achieve the necessary threat landscape visibility. Using canaries, honeypots, basic SIEM solutions, and other threat management tools could constitute an affordable cybersecurity alarm system. And its silence, given it is appropriately configured and always on, might be another tangible indicator of your return on investment in cyber security.

3. You Pay Others to Hack You, and They Have a Hard Time
The third way to ensure you do good in cybersecurity investment is to hire professional hackers to challenge your defenses. There is a large cybersecurity market for penetration testing services, and these ethical hackers are ready to simulate real-world cyberattacks and report how well you detect and prevent them.
Finding a good penetration testing firm may be difficult, but once you find a capable team, it becomes your personal return on security investment calculator. If you found an amazing pentesting team, chances are they will hack you a few times no matter how hard you try to prevent that. But do not worry: it is okay if it gets worse before it gets better; after all, this is what you pay them for.
After getting a pentesting report from them and making all recommended fixes and adjustments, you will see immediate results. After a few iterations, you will be able to measure your progress and incorporate it into your management reports. And at a point, you may find yourself in a situation where your pentesting firm praises your efforts and recommends raising the bar and trying out more sophisticated red teaming exercises instead of classic pentesting.

4. Everyone Pays High Insurance Premiums, and You Don’t
Cybersecurity insurance is an outstanding risk management tool: it is better to have it than to not have it, and it is best to have it and not use it. There is a catch, though: in recent months, as cybercriminals have expanded their operations, the insurance premiums have skyrocketed.
Year over year cyber insurance was as inexpensive as it was unpopular. The only viable cases for cyber insurance were certain compliance requirements that simply demanded that large international companies insure the risks of cyber security incidents. Until about three years ago, an average organization’s chances of getting hacked were relatively low, but now ransomware has changed it.
If before, to get hacked, you needed to do something valuable or important, now the only prerequisite is a stable internet connection. Nowadays, cybercriminals don’t spend time selecting targets. Instead, they hack everything they can and “calculate the ROI” later.
The insurance market reacted, and during the last six months, the 50% increase in ransomware (and a constant 9% monthly increase in the first quarter of 2021) has changed the insurance pricing. If before virtually everyone could afford cyber insurance with zero due diligence, now you will have to pay much higher – in some cases tenfold – premiums. Insurance underwriters incorporate the change in the risk landscape into their products, and the changes are not to your advantage.
Unless, of course, you can demonstrate that your cybersecurity risks are significantly lower than in other companies. Proper risk management results in lower residual risks left to insure, which means lower premiums. The logic is simple: show the insurance company that you did your homework, and they will provide you the same coverage for a lower fee. If that does not fit the return on security investment definition, we don’t know what does.

5. When You Get Hacked, It Is not the End of the World
As every security professional knows, there is no question if you could get hacked, there is a question of when. Accepting an incident’s inevitability is a simple truth one has to embrace early in their career. In the end, amateurs try not to get hacked; professionals try not to stay hacked. So, if you did everything right, if you have an incident response plan, and everyone knows the drill when the incident finally happens, the company comes prepared.
You have your security operations in place to reveal and localize the incident; your incident response team is ready to engage; all employees know how to deal with the temporary unpleasantness of the crisis; lawyers have their law enforcement contacts at their fingertips; top managers and PR have the texts ready for release. Even the red team is prepared to learn from the occasion and integrate it into their future work. And the most important of all is that everyone, including you, has lower stress levels along the way.

Conclusion
These are the five most straightforward ways to demonstrate that the companies investing in cyber security are doing a good job without calculating the return on security investment (ROSI). A proper application of cybersecurity economics allows you to streamline this process and integrate it into your business planning and reporting processes.
We at BSG are always happy to assist you in meeting your security objectives in an optimal way. While throwing money at the problem never really helps in this industry, we know that this is what many companies frequently do. Unfortunately, there are plenty of security vendors that benefit from such an approach and promote it in the market.
We help organizations and security managers build the necessary strategic awareness of cybersecurity in a business setting. To know more about our strategic cybersecurity workshop, get in touch by email at hello@bsg.tech.