OWASP Top 10 Project has issued the release candidate of its 2021 version of the famous appsec risks rating for open discussion. I have read it with great pleasure and I want to share some of my thoughts. tl;dr: I like it very much, and I wish it would not change until the official release, except for a minor nuance of SSRF occupying A10.
A bit of history from an OWASP insider. OWASP Top 10 is, by all means, the best-known OWASP Project. For some inexperienced audiences, it is equivalent to the whole OWASP. This is incorrect, of course, but it is nonetheless the case.
We have a joke among OWASP members, it goes like this. While our target audiences are software developers, managers, and security professionals, most of these people don’t know what OWASP is. But those who think they know what it is, think it’s OWASP Top 10.
Jokes aside, OWASP Top 10 has a massive impact on the industry. And like many influential things, this impact is good when the tool is applied correctly and not so good otherwise.
The reason for the negative impact of the Top 10 is simple. Many readers treat OWASP Top 10 (2017 and prior) as a security standard, which it is not. Top 10 is instead an awareness material written, structured, and illustrated to introduce Application Security to the interested audience. It contains information about the most prevalent application security risks. But adherence to it as a standard does not guarantee any substantial security. Simply because it is a Top 10 of hundreds of security risks, some of which could be much more severe than those that made it to the top.
Nonetheless, it is neat and nice and useful, which is why it is so popular. As a result, it is catchy, which brings the marketers in. Lo and behold, we have OWASP Top 10 Security Audits, Vulnerability Scanners, and Penetration Tests offered by security vendors and consulting companies. This is absolute nonsense, but who cares? The OWASP successful brand name and its flagship project sell well, and there are people eager to exploit the situation. It often becomes absurd when companies announce tenders with a requirement to conduct a network and social engineering pentest according to OWASP Top 10. Or even more so when customers ask if an OWASP Top 5 pentest would be twice cheaper than the OWASP Top 10 one.
So, as bad as it gets, OWASP Top 10 is a de facto standard used or rather misused by many people. And here comes the magic trick. The changes in the OWASP Top 10 2021 version make it applicable as an actual security standard. For instance, they have added a whole Insecure Design section and some conceptual threats often overlooked by development teams. Because, let’s face it, for many of them, application security starts with a third-party pentest.
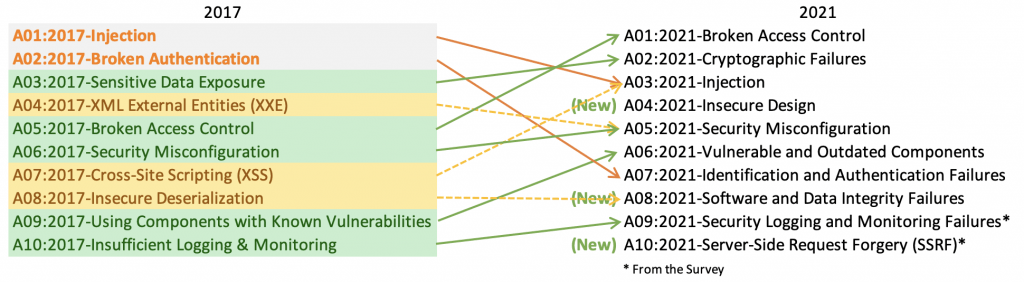
The Top 10 2021 is more mature as a standard, or better to say, it finally resembles a standard. And I am sure that this fact is already causing a lot of pain and suffering to the marketing people. How would your cloud vulnerability super-duper next-generation magick stick scan for weak or insecure logging (A09) or insecure architecture design (A04)? One damage control strategy could be announcing that 2021 is too high-level and the solution sticks to 2017. Or implementing only a subset of tests and calling it a day. I am all attention, and I am stockpiling popcorn, waiting for the show to begin.
As I said, I am a big fan of OWASP Top 10 2021. The deliverable is so next-level, I cannot describe it in words. The wording, writing style, ease of comprehension are paramount. The elegance of introducing new concepts to a reader is unprecedented. The progress is evident, inspiring, and delightful to my eyes. And if sneaking it into the broadest possible adoption and then upgrading to a fully-fledged cybersecurity framework was actually intended, I salute the project team’s social engineering and strategic planning skills. Sun Tzu would be proud of you.
I am eager to use OWASP Top 10 2021 in our work at BSG, and I cannot wait for its official release. Take care.
