Summary
We have just wrapped up a whirlwind year that tested our ability to unite and rise to the challenge of these trying times. But here we go! 2020 was quite a ride, but it has shown us the Berezha Security team’s real efficiency along the way. We are impressed by our achievements, and we are happy to share them with you, especially our report on security vulnerabilities.
During 2020 we broke a bunch of personal records, such as the annual and monthly revenue, the total yearly projects, and the number of projects we ran simultaneously. As a result, we now know that it was a good year and the best in BSG history.
In 2021, we start a tradition of issuing this annual report. Last year, we counted our critical security vulnerabilities, learned our lessons, and shared some of them with you in this blog post. We believe that this information helps all readers of this report, so we put it in here along with the business-related BSG data.
Why 2020 Was a Different Year
The COVID-19 pandemic has changed the risk profile of the majority of our clients. Due to the coronavirus, companies were rapidly shifting towards Work From Home as a new normal. For the same reason, the business technology trends of last years have accelerated. Companies focused more on automation, going cloud-native and adopting cloud infrastructure, and digitalizing virtually every aspect of their operations.
In Berezha, our work has changed too, although not much. Since day one, we have no infrastructure “on the ground,” so the WFH part was easy. Nonetheless, we had to cut off all on-site activities and find new ways of achieving virtual presence where required.
BSG Goals
At the beginning of each year, we develop new strategies and set business objectives. Last year, we had achieved a series of internal and external accomplishments and introduced some significant changes.

1. Project management function
Successful teams grow, and large teams require coordination. Our work culture and approach to project delivery make it easy for project leads to manage the teams and timely deliver high-quality results. But on a larger scale of inter-team cooperation, we needed a general coordination role.
The team indicated a lack of formal PM function and we strengthened it by one of our co-founders.
2. Marketing strategy initiation
Our brand – the Berezha Security is quite known on Ukrainian cybersecurity market.
But we strive to move our business forward and become a global brand in the nearest future.
That is why, after five years of growth following word of mouth, client references, and good reputation, we have decided to accelerate that and establish a formal marketing business function.
Following the creation of the Chief Marketing Officer role, we will reassess all our business activities and build a solid strategy going forward. We have already developed a new brand and initiated the new website development. You will see more of our new BSG face in just a couple of months.
3.Threat Modeling in every new project
In BSG operations, we never stop innovating by combining our experience, social activities, and professional contribution. Last year we experimented with introducing Threat Modeling into every appsec project. This way, we aimed at bridging the gap between the scope of work and clients’ expectations.
The security assessment completeness is a vast industry problem yet unsolved in many companies. Testing guides and accompanying checklists try to solve it but cover just a portion of the scope. Using Threat Modeling, we make sure that all things that could go wrong are brainstormed and accounted for before we start simulating them.
4. Introducing DARTS: Dynamic Application Red Team Simulation
Like many, we have a long history of using various highly secure note-sharing apps for team collaboration. These tools are far from perfect, most of them make you choose between security and efficiency, and we felt like it blocks our growth. It is why we have decided to invest in the development of a new platform that will allow us and our clients to work securely and efficiently on the pentest data.
This DARTS initiative will streamline and simplify all project activities, automate report generation, and integrate external data sources. We already use it in most project phases and are working on integrating it with our toolkit.
5. Initiating BWAPT: Berezha Web Application Pentester Training
In 2020, we transformed the experience of our team into a professional training program. Our team members volunteer at professional initiatives, such as OWASP and NoNameCon, as individuals. But now our company has a fair share of this professional contribution as well.
The BWAPT professional training program focuses on applied skills that we use during the security testing projects. Starting from the early project steps, through all the phases, up to reporting, we describe what we do and how we do it. All BWAPT lessons are taught by real practitioners who are knowledgeable and experienced in those areas.
BSG Growth Indicators
In BSG, we use various business effectiveness indicators, but we would like to hold those back for now as we are still a private company. However, our general changes in the scale of operations we summarized in these two values.
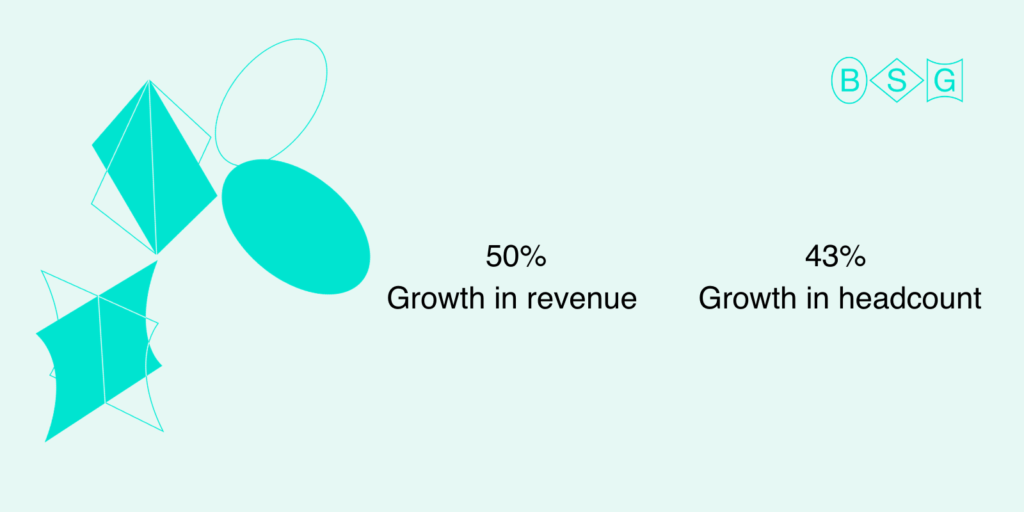
Growth in revenue: 50%
Our total revenue in 2020 has increased by 50% compared to the previous year. We have also experienced a series of the most intense and profitable months ever closer to the year-end. Overall, the annual business trends remained the same: constant growth with two slight declines in the middle of winter and at the end of summer.
Growth in headcount: 43%
Despite the COVID-19 pandemic, we continued to grow our team: in 2020, we welcomed three new colleagues. Simultaneously, we did not put salary raises on hold and continued to reward our teammates for their professional contributions in line with the BSG policy.
Projects and clients review
Service delivery
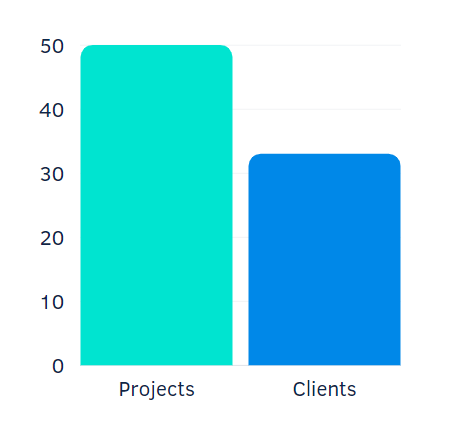
In 2020, the BSG team completed 50 projects for 33 clients. It means that every second client requested our services recurrently. The projects-to-clients ratio demonstrates our strong customer retention, as, after the successful initial project, the majority of our clients become regulars.
Project types
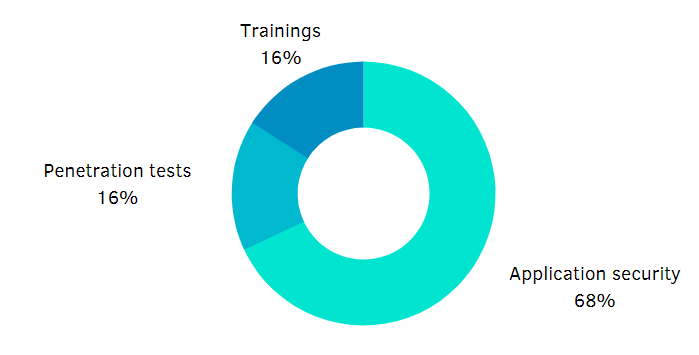
The trend in the application security assessments popularity only strengthened in 2020. Application pentests remain our main priority, and we continue developing our appsec expertise by learning from the best, teaching others, and building new knowledge ourselves.
Classic penetration tests were way less popular in 2020, mainly due to a steep decline in demand for internal pentesting for apparent reasons. Instead, more companies requested objective-based pentests that follow a specific scenario du jour, e.g., getting access to the enterprise network via VPN.
We delivered fewer corporate training sessions than last year, and most of them were application security awareness programs for developers. However, we have developed our brand-new web application pentester training program and already had two student groups complete it.
Project geography
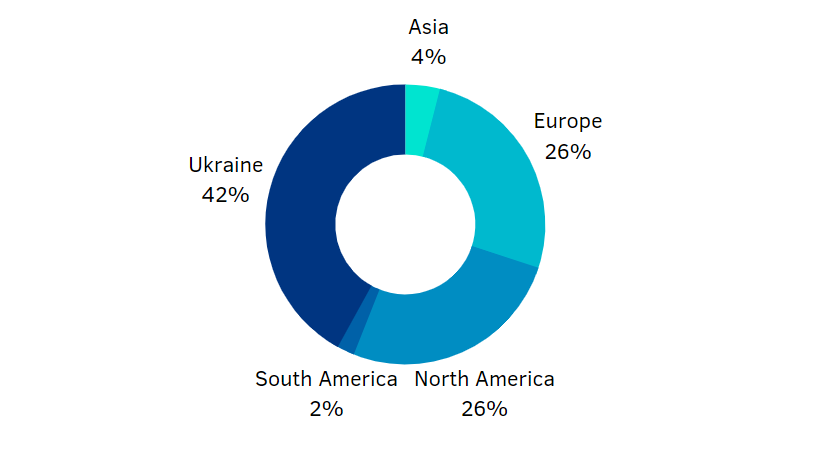
This year, we can proudly state significant growth in the number of projects we do for Ukrainian companies, as more and more organizations introduce high tech solutions into their business operations. As a natural consequence, the demand for protection against cyber threats is now more actual than ever.
Of course, we observe a strong bias here. All Ukrainian clients are either high-tech firms in the areas such as software product development and IT services or fintech companies in banking and online payment. Of course, most of them are integrated into international business structures.
No less important target, we have started our development, covers Europe and North America. We have solid expertise with many global clients, so, 2021 year is dedicated to reaching new targets and global markets!
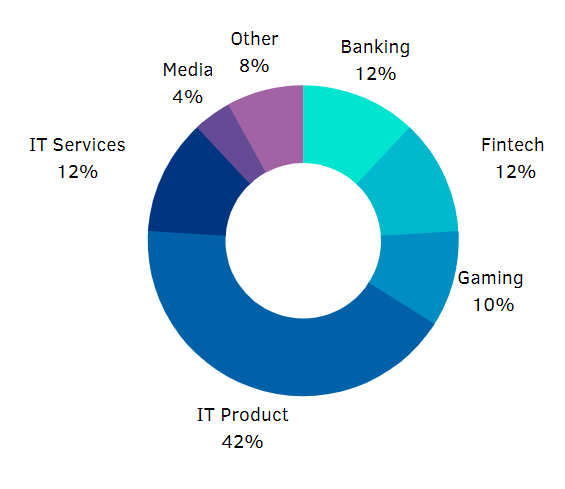
Projects by industry
Our projects by industry trends did not change in 2020. The IT product development clients keep the lead and care the most about their security and clients’ data. They were followed by the Fintech and Banking organizations, which are slowly but surely exploring the opportunities presented by security companies in Eastern Europe.
- Banking
- Fintech
- Gaming
- IT Product
- IT Services
- Media
- Retail
- Groups of Private Individuals
BSG Security Findings
Now to the technical stuff. This year we decided to extend the amount of information we share about our security findings. In the following pages, you will see how many security vulnerabilities of different types and risk levels we found, how fast our clients fixed them, and some average values around those processes.
We have aimed to make this report as general as possible to avoid any harm to our clients. Thus, the amount of details that we could share is limited. Nonetheless, we believe that this data may help our customers compare their security posture to other companies and the industry in general.
And of course, to our future clients, this data may show the BSG team’s efficiency. In other words, if you are looking at working with us, this is what you will most likely get.
Findings by risk level
In the BSG operations team, our motto is: not reporting the BS. More politely, if a scanner-generated vulnerability does not require fixing, we will omit it. In our opinion, the length of the report is not what our clients truly need. Instead, they need concise vulnerability descriptions, correct evidence, clear recommendations, and straightforward steps to reproduce. We value clarity, brevity, and repeatability in our work, and we think it is why our clients chose us in the first place.
322 in total
In 2020 we reported 322 bugs in total. Let us drop this figure down by risk level and other essential issue parameters.
By risk level
- Critical – 19
- High – 32
- Medium – 99
- Low – 172
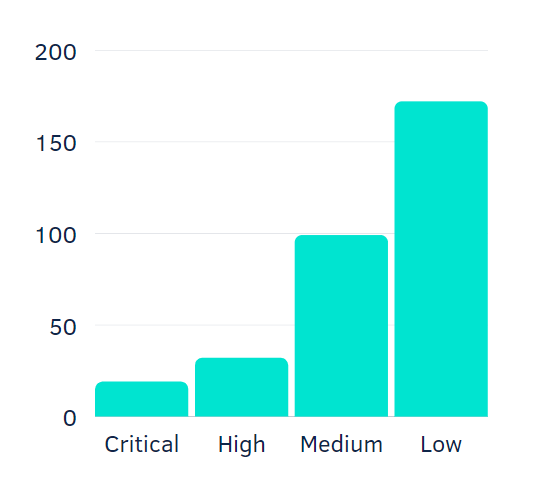
The issue risk level helps our clients prioritize the fixes. We report Critical vulnerabilities in real-time, so the clients can start remediation even before the project is over. High-risk vulnerabilities demand close attention in the next few days after getting the report, while Medium-risk issues may wait a couple of weeks. Low-risk findings are potentially harmful or can be the building blocks for more sophisticated attacks. But you still must fix them: remember, if it is not essential, we do not put it in the report.
How clients fix security vulnerabilities
Our reports are subject to a grace period: the client can get one free retest of all issues if they fix them in the next 60 days. In this way, we are trying to accelerate the remediation.
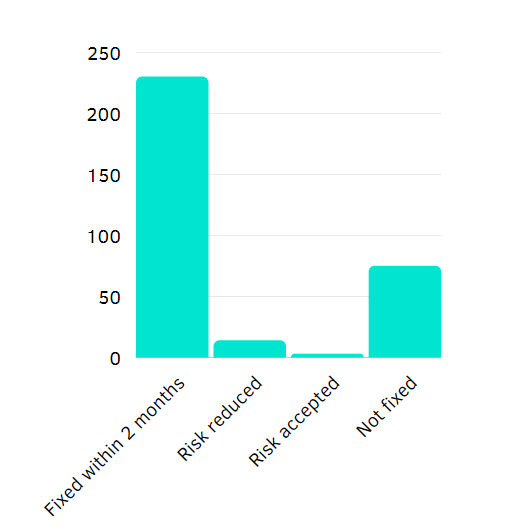
Coming back next year and finding the same issues in the same places is the worst pentester’s nightmare. On the other hand, who are we to demand fixes from clients? This is why the incentive we give is purely economic: fix everything fast and get retested for free. And it appears to work: the majority of fixes – 230 or 71% – are applied within the grace period.
- Fixed within two months – 230
- Risk reduced – 14
- Risk accepted – 3
- Not fixed – 75
Fixing the security vulnerabilities
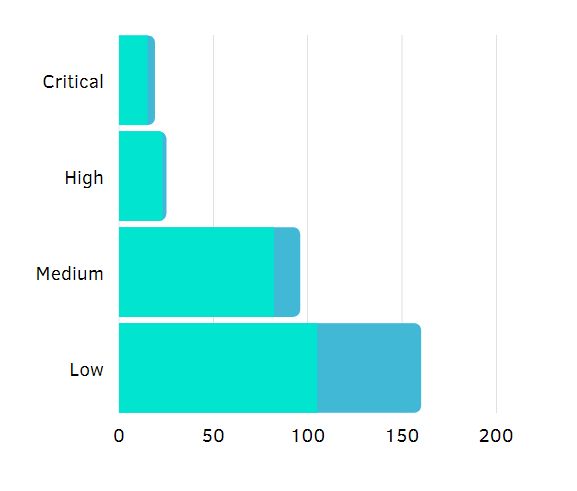
The non-fixed issues were mostly low-risk, and the accepted findings were left unfixed after a well-informed management decision.
Below is the chart, which showcase the amount of fixed/non fixed issues.
- Critical – 15/4
- High – 23/2
- Medium – 82/14
- Low – 105/5
Number of bugs on average
We think this may be the most critical information in this report for managers and security leaders.
First, if you are already one of our clients, you can compare yourself to others without exposing their secrets. We often say at pentest debriefs that a specific report has more or fewer issues than usual. Now you know what “usual” means.
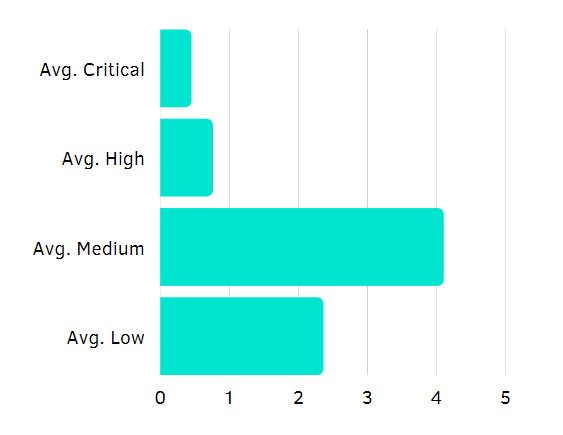
Second, if you weigh the pros and cons of doing a pentest with us, this might give you a perspective of what you can expect in the report. We found, that on average each BSG report contains 7.66 bugs, where:
Average Critical, per report – 0.45, High, per report – 0.76;
Average Med, per project – 4.10, Low, per project – 2.36
Top 10 critical bugs
When we find a critical vulnerability, we report it out immediately. It means that our client does not have to wait for the pentest to end to start fixing the bug. Criticals are the most dramatic and exciting encounters for us during the year. Here is the list of the riskiest ones.
1. Sensitive Information Disclosure
It comes in many forms but always means that we have managed to access some secrets lying around. When we discovered logins and passwords to highly privileged accounts or confidential databases, some of these cases were critical. And the majority of critical bugs were of this type.
2. Remote Code Execution (RCE)
RCE is a type of bug that every pentester and bug hunter dreams of. Finding it means there is a way to compromise not only the application we are testing but the infrastructure below it, which in most cases bears the highest risk and pays out pretty well in bug bounties. Last year we found a few.
3. Cross-Site Scripting (XSS)
Any vulnerabilities chart would be incomplete without the XSS. Although it is a client-side bug that targets the web application users and not the app owner, critical XSS can lead to a user account takeover and an ability to run arbitrary JavaScript code with that user’s permissions. When the target user is an admin or another high-profile account, the XSS is critical.
4. Broken Authentication
Broken authentication always means a way to circumvent some part of it: guess usernames, pick passwords, turn off two-factor authentication, etc. Critical cases include complete authentication bypass or anonymous access to critical data or functions. During a pentest, findings like this do not let us sleep at night, so we urge our clients to start fixing the same hour we find them.
5. Broken Business Logic
Unlike most vulnerabilities usually exploited by malicious hackers, business logic bugs are discrepancies in application checks and balances that could be abused by its regular users. Security against your own customers is a real thing, and it costs real money. Last year we could manipulate the price of goods, transfer negative amounts of money, and create tens of users in the subscription plans that allowed just a few.
6. Broken Access Control
Access control is key to any security policy, and it very often goes wrong. Usually, the developers or admins simply allow excessive permissions to an unnecessarily wide variety of subjects. As a result, anyone logged into the cloud platform can read, write, or otherwise access the restricted areas. When these areas store sensitive data, such as software updates or legal documents, the issue becomes critical.
7. Lack of API Rate Limits
This type of bugs makes news only if there is a way to abuse it to cause a Denial of Service condition or, as in the critical case, brute force username, password, or two-factor authentication code. This threat is relevant to most apps we test, and we simulate it quite successfully. When we can use this issue to gain access to a high-privilege account, it is critical.
8. Insecure Direct Object Reference (IDOR)
When one user, say patient, can suddenly read the data of other users, such as other patients and even doctors, often en masse. The prevalence of this bug is surprising for many, but for us, it is rarely unexpected. In most cases, developers just turn off the authorization checks in a test software version to speed up the testing procedures and then forget to turn it back on before moving to production.
9. Server-Side Request Forgery (SSRF)
A rare, elite bug that allows us to make the server-side of the app do things we tell it to do. As the RCE, although less often, it can lead to a complete compromise. We can usually at least map internal network segments and try to exfiltrate sensitive data from the otherwise unreachable locations. But when we can do more, it becomes critical very quickly.
10. Insecure Configuration
Insecure configuration means that admins or DevOps could do something right, but for some reason, did not. From the Active Directory domain configuration to the Amazon Web Services account policy, insecure settings can lead to devastating incidents. It does not relate to software updates, though, as they usually open avenues for attacks that use other types of critical vulnerabilities.
Top 10 popular bugs
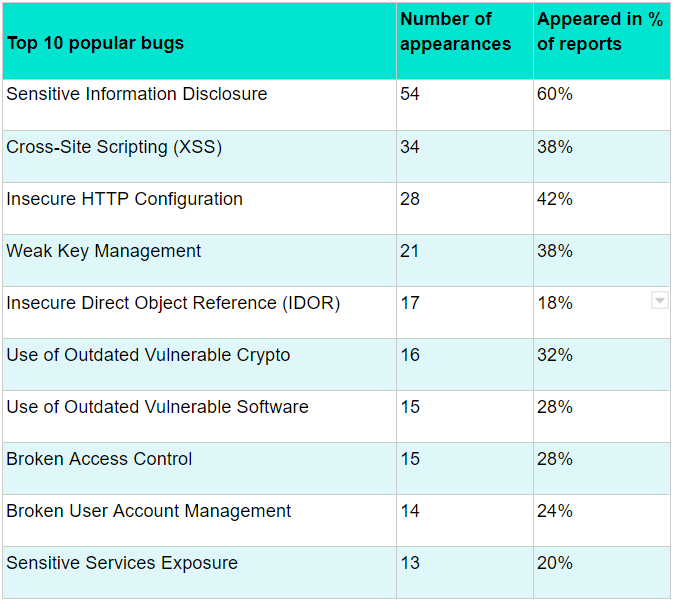
Bugs’ popularity may look like irrelevant data that does not carry much business sense. But in fact, knowing what bugs are more widespread can help you align expectations of security threats. Which in turn could help chose and implement relevant countermeasures. Let us go through these issues one by one and discuss why they are at the top of popularity.
As we said earlier, Sensitive Information Disclosure comes in many forms, which is why it is so popular and appears in 60% of reports. Preventing these issues demands high discipline in data protection and configuration management. Also, often you just need to encrypt stuff, which introduces a lot of additional tasks, such as key management and protection.
XSS is the second widespread bug present in 28% of reports. No surprises here; data validation is hard and sometimes absent at all. Getting rid of XSS (and many other input data related bugs) is fairly straightforward: just do not trust what you are taking in and out of your application.
Insecure HTTP Configuration means that the application does not use security-related HTTP headers, uses them in a wrong way, does not protect security-related cookies from interception and abuse, or otherwise misbehaves. Remediating these issues is easy and is usually done at the configuration level.
Weak Key Management is a general class of vulnerabilities that make stealing, predicting, picking, or guessing secret keys way easier than required. Fixing weak key management depends on the specific issue, and there is no silver bullet. But in general, making passwords and other keys unique, long, random, and well-protected solves the problem.
IDOR is the second most popular appsec bug after XSS. Checking privileges across user roles, combined with accurate session management, can lead to robust protection. However, you can never be sure you protected all endpoints and pathways. The good news is, testing for broken authentication is fairly simple; it is just a lot of work.
Use of Outdated Vulnerable Crypto and Use of Outdated Vulnerable Software pop up when you do not regularly update the stuff you use. With software, it is less of a problem, as many vendors have introduced a way to automatically update their products. The crypto part may be hard, though, as keeping it up to date may raise compatibility issues.
Broken Access Control is another general term that covers all sorts of errors in planning and implementing various kinds of security policies. The most widespread instance of this vulnerability is the loosely configured web directories, file servers, and S3 buckets. The risk level here depends on the kind of data in the poorly protected storage.
Broken User Account Management means that there is a way to change or update user credentials insecurely. Sending account recovery links to arbitrary emails, setting a new password without knowing the old one, turning off the two-factor authentication – these are a few examples.
Sensitive Services Exposure happens when a service that demands security does not get it. It becomes a considerable problem when this service has some other flaw, such as broken authentication or vulnerable software version. Public exposure of such services may lead to data leakage, but it falls into this category before it actually does.
Conclusion
We hope you enjoyed reading our annual business and vulnerabilities report for 2020. We expect the information in this report will help you better plan for the cybersecurity challenges. Let us summarize the key takeaways of 2020.
Key takeaways
The 2020 year showed us the real productivity and efficiency of the Berezha Security team and what a first-class team of professionals we gathered!
A continuous increase in our operations’ volume and efficiency has shown us our resilience and ability to rise to the challenge and succeed despite the odds.
During 2020 we broke a bunch of personal records, such as the annual and monthly revenue, the total annual projects, and the number of projects run simultaneously.
The main accomplishments in 2020
1. Project management
We have established a formal project management function at the highest level of the company.
2. D.A.R.T.S.
We have started developing our own pentest process automation platform, and our clients are already benefiting from it.
3. Threat Modeling in pentests
We have built-in the Threat Modeling in all our offensive security projects to achieve and demonstrate full coverage of works.
4. Marketing strategy
We have initiated the first corporate function, and it is Marketing. You will see more of our new BSG brand soon.
5. BWAPT
We have developed our first professional training program, and it had great success with two student groups.
The new brand
2020 has become a time of significant changes. Berezha Security is stepping into the new business development phase and discovering new markets in Europe, Asia, and the Americas.
With these plans in mind, we have revisited our brand and decided to transform it from a genuinely Ukrainian trademark to a worldwide image. After in-depth research and market analysis, we have built the new BSG brand book. We believe Berezha Security’s rebranding will enable our expansion and help us deliver a more fruitful customer experience.
Our company name will change soon from Berezha Security to an extended form of Berezha Security Group, abbreviated as BSG. Shortly, you will start seeing updates to our identity on the website, social media, and elsewhere.

Stay in Touch
Thank you for reading our annual business and vulnerabilities report. If you have any questions regarding this report, please contact us on our website or by email: hello@bsg.tech.
To stay in touch and follow our weekly updates, subscribe to our Facebook, LinkedIn, or Twitter.
Stay safe.

Pingback: Звіт про вразливості безпеки знайдені у 2020